A regular domain user can easily take over the entire Active Directory domain.
While we still recommend that the print spooler service should be disabled on any system that does not need it, we also want to provide a temporary workaround to make the exploit ineffective, while allowing you to keep your print servers running, until a patch is available.
The exploit works by dropping a DLL in a sub-directory under C:\Windows\System32\spool\drivers
By restricting the ACLs on this directory (and sub-directories) we can prevent malicious DLLs to be introduced by the print spooler service.
At the moment, we are not aware of any way to force the DLL to be dropped in a different location.
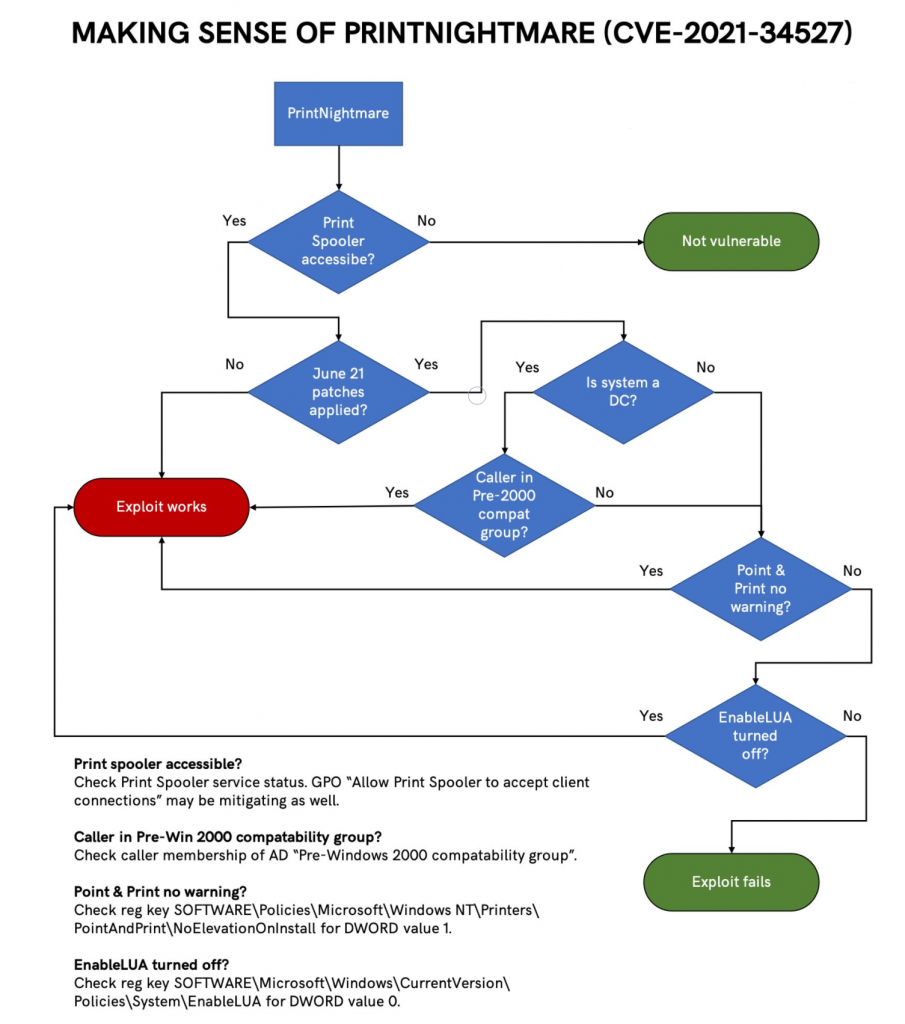
Restricting the ACLs
The following PowerShell script will do the trick.
$DPath = "C:\Windows\System32\spool\drivers"
$AccessList = (Get-Item $DPath).GetAccessControl('Access')
$SObj = New-Object System.Security.AccessControl.FileSystemAccessRule("System", "Modify", "ContainerInherit, ObjectInherit", "None", "Deny")
$AccessList.AddAccessRule($SObj)
Set-Acl $DPath $AccessListThis will add a Deny rule for the drivers directory and all subdirectories, preventing the SYSTEM account to modify its contents.

Deny rule on the drivers directory and subdirectories
If administrators need to perform configuration changes that require the service to write in these directories, this rule can temporarily be removed, and re-added after the change.
To remove the ACL we just added
$DPath = "C:\Windows\System32\spool\drivers"
$AccessList = (Get-Item $DPath).GetAccessControl('Access')
$SObj = New-Object System.Security.AccessControl.FileSystemAccessRule("System", "Modify", "ContainerInherit, ObjectInherit", "None", "Deny")
$AccessList.RemoveAccessRule($SObj)
Set-Acl $DPath $AccessListThis is not a perfect solution, but until a patch is available, it is a way to keep the print server running in cases where it is strictly necessary.
We have verified that the ACL prevents the successful execution of the following exploit implementations:
- https://github.com/cube0x0/CVE-2021-1675 (both C# and Python implementations)
- https://github.com/afwu/PrintNightmare
why system account is enough, because Spoolersv.exe running uneder System account privileges, so by deny access to this account spoolersv.exe can not modify this folder, while the vulnerability need spoolersv.exe upload a DLL into this folder.
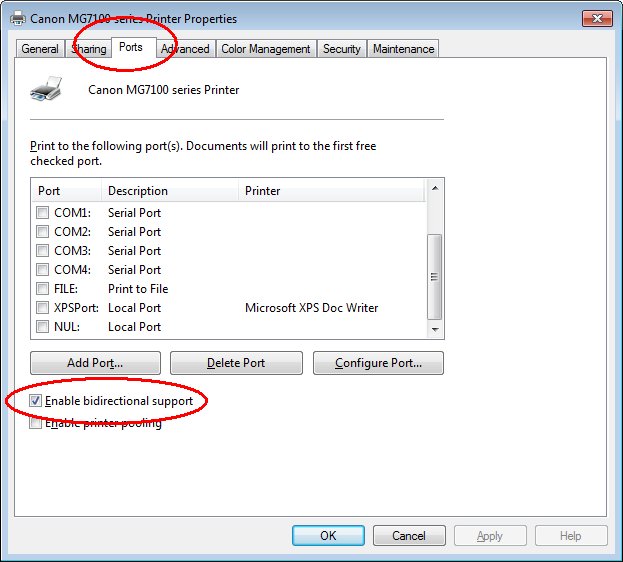
Make Sure “Enabled bidirectional support” unchecked, means it’s Disable.
The setting, found on the Ports tab when looking at the Printer Properties menu in Windows, controls whether a print driver will communicate with the physical printer to determine the printer’s state and find out details like whether a finishing unit is attached. The exact function will vary depending on the make and model of printer.


Superb and also really exciting blog. Will certainly review much more from
now on.