This blog post will walk you through the steps of remotely capturing traffic from a domain controller and then analyzing it locally. This can be useful for troubleshooting network issues or investigating security incidents. Requirements A Windows computer with PowerShell The NetEventPacketCapture PowerShell module The etl2pcapng PowerShell module A domain …
Read More »very simple modifications to a Meterpreter shellcode dropper can be sufficient to bypass modern EDRs
Introduction When I talk about EDRs in this article, I mean a combination of endpoint protection (EPP) and endpoint detection and response (EDR). I also want to define the term “evasion” in the context of EDRs and malware. When I talk about the fact that it is or has been …
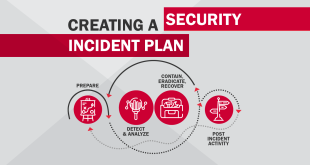
Read More »Incident Response Playbooks and Workflows
Incident-Response-Playbooks-and-workflows-1Download
Read More »NTLMRelay2Self over HTTP (Webdav)
Just a walkthrough of how to escalate privileges locally by forcing the system you landed initial access on to reflectively authenticate over HTTP to itself and forward the received connection to an HTTP listener (ntlmrelayx) configured to relay to DC servers over LDAP/LDAPs for either setting shadow credentials or configuring …
Read More »Cobalt Strike Defense Guide – 2
In previous report on Cobalt Strike focused on the most frequently used capabilities that observed. In this report, we will focus on the network traffic it produced, and provide some easy wins defenders can be on the look out for to detect beaconing activity. We cover topics such as domain fronting, …
Read More »Malicious Document Analysis [Episode 1]
Before starting the analysis, I’m going to use the following environment and tools: REMnux: https://docs.remnux.org/install-distro/get-virtual-appliance Didier Stevens Suite:https://blog.didierstevens.com/didier-stevens-suite/ Malwoverview:https://github.com/alexandreborges/malwoverview Furthermore, it’s always recommended to install Oletools # python -m pip install -U oletools All three tools above are usually installed on REMnux by default. However, if you are using Ubuntu …
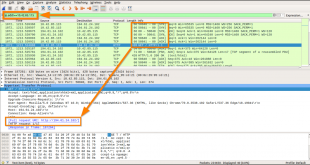
Read More »PCAP Analysis
Learning Objectives Understand the advantages and goals of PCAP AnalysisHow to pivot into and away from PCAP Analysis (how to use findings for quicker analysis)Common tools to useHow data reduction aids in investigations Common Tools SnortTcpdumpWireSharkTShark Tools Covered Here SnortTcpdumpWireshark Notes Keep solid notes on your thinking around evidence and …
Read More »Incident Response without Windows Event Logs
This post discuss some Digital Forensics and Incident Response (DFIR) techniques you can leverage when you encounter an environment without Windows event logs. Where are the logs? at work, we regularly respond to security incidents with ineffective logging and auditing for the purposes of a cyber incident. In some cases, …
Read More »How To Attack Kerberos
Kerberos Fundamentals Kerberos is a network authentication protocol that works on the principle of issuing tickets to nodes to allow access to services/resources based on privilege level. Kerberos is widely used throughout Active Directory and sometimes Linux but truthfully mainly Active Directory environments. TLDR: https://www.roguelynn.com/words/explain-like-im-5-kerberos/ I am aiming to approaching …
Read More »RDP Authentication Artifacts for DFIR Purpose
A good detection technique to spot Remote Desktop Connections that are exposed to the internet is to scan RDP event logs for any events where the source IP is a non-RFC 1918 address. This provides you a good way to check for locations that may be port forwarding RDP, like …
Read More »