Just a walkthrough of how to escalate privileges locally by forcing the system you landed initial access on to reflectively authenticate over HTTP to itself and forward the received connection to an HTTP listener (ntlmrelayx) configured to relay to DC servers over LDAP/LDAPs for either setting shadow credentials or configuring …
Read More »Yearly Archives: 2022
ISO 27001 Controls Ultimate Guide – Updated for 2022
In this ultimate guide to the ISO 27001 controls we are going to explore the security control requirements. We will go through the ISO 27001 controls, the old version of the ISO 27002: 2013 controls and the new and updated ISO 27002: 2022 control list. What controls do you need …
Read More »Cobalt Strike Defense Guide – 2
In previous report on Cobalt Strike focused on the most frequently used capabilities that observed. In this report, we will focus on the network traffic it produced, and provide some easy wins defenders can be on the look out for to detect beaconing activity. We cover topics such as domain fronting, …
Read More »Malicious Document Analysis [Episode 1]
Before starting the analysis, I’m going to use the following environment and tools: REMnux: https://docs.remnux.org/install-distro/get-virtual-appliance Didier Stevens Suite:https://blog.didierstevens.com/didier-stevens-suite/ Malwoverview:https://github.com/alexandreborges/malwoverview Furthermore, it’s always recommended to install Oletools # python -m pip install -U oletools All three tools above are usually installed on REMnux by default. However, if you are using Ubuntu …
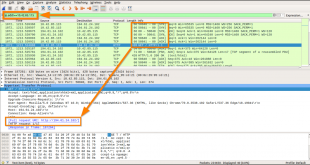
Read More »PCAP Analysis
Learning Objectives Understand the advantages and goals of PCAP AnalysisHow to pivot into and away from PCAP Analysis (how to use findings for quicker analysis)Common tools to useHow data reduction aids in investigations Common Tools SnortTcpdumpWireSharkTShark Tools Covered Here SnortTcpdumpWireshark Notes Keep solid notes on your thinking around evidence and …
Read More »