To compare Active Directory accounts against breached passwords you need access to your Active Directory with a specific privileged account, a password list with NTLM hashes and some PowerShell commands.
But why should you do this?
- Password hashes of Domain accounts can be dumped locally from SAM, memory, remotely and as well just with Windows built-in features (memory dump).
- Users with well known passwords (compromised passwords) are extremely easy to “recover” by using password lists
- Therefore the passwords of these accounts must be changed to reduce the risk of getting easily “hacked”.
Password list
As the download of the password list could take a while, start downloading the latest version from: https://haveibeenpwned.com/Passwords
Make sure to download the NTLM password list (version 4 or newer).
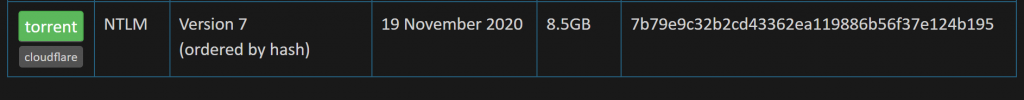
When finished, extract the file: I’m using C:\temp\pwned-passwords.txt as target.
Export password hashes from AD
You do not have to be a member of the Domain Admins, Enterprise Admins or the Administrators group, but you need the “Replicating Directory Changes All” permission on Domain level.
Install PS Module
Now launch PowerShell and run:
Install-Module -Name DSInternals
More info about module: https://www.powershellgallery.com/packages/DSInternals/
Set credentials
Now you have to run another command in PowerShell, then enter the credentials which are delegated on Domain level with ReplDir permissions:
$mycredentials = Get-Credential
Enter credentials
Export users and password hashes of all users to file
Run the following command within PowerShell to “pull” all account information from the Domain Controller of your choice. When finished, the hashes are saved in the file c:\temp\hashes.txt
Get-ADReplAccount -all -NamingContext “DC=Domain,DC=local” -Server Domaincontroller.domain.local -Credential $mycredentials | Format-Custom -View HashcatNT | Out-File c:\temp\hashes.txt -Encoding ASCII
Make sure to change Domain name and Domain Controller!
Compare it…
Download PowerShell script from https://github.com/DGG-IT/Match-ADHashes/ and save the file to c:\temp\
Load function and compare hashes
Run the following command to load the function:
.\Match-ADHashes.ps1
Make sure you run it from c:\temp
Start comparison:
$list = Match-ADHashes -ADNTHashes C:\temp\hashes.txt -HashDictionary C:\temp\pwned-passwords.txt
save result to a list
Export into CSV
Write output to a CSV file:
$list | select Hash,Frequency,@{Name=’user’;Expression={[string]::join(“;”, ($_.user))}} | Export-Csv -Path c:\temp\report.csv -Delimiter ‘;’ -NoTypeInformation
Result
Open the CSV and make sure to remediate all accounts. Set priority on privileged accounts. These must be changed immediately!